Topologies: A topology is the layout of the network.
Bus topology:
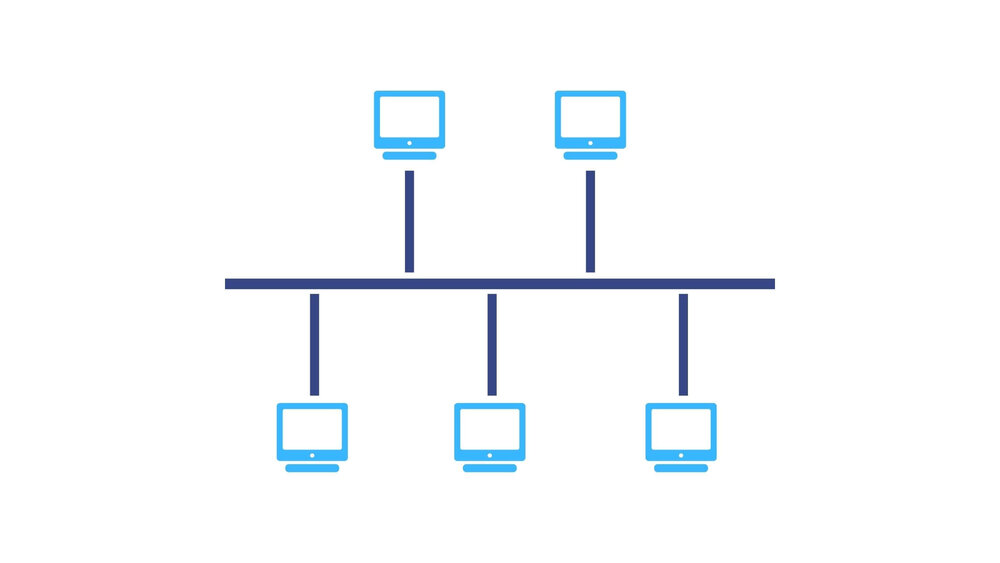
All devices are arranged in a line and connected to a single cable. Devices send data in both directions. Because of this, it causes data collisions which slows the network. If the cable fails, then the whole network fails.
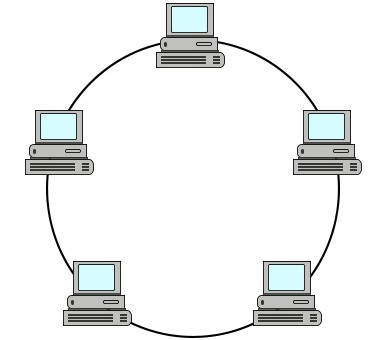
Ring topology: Data moves in one direction around the ring. This prevents data collisions.
But only one device can send data at a time and data passes through many devices before reaching its destination. This makes the network slow.
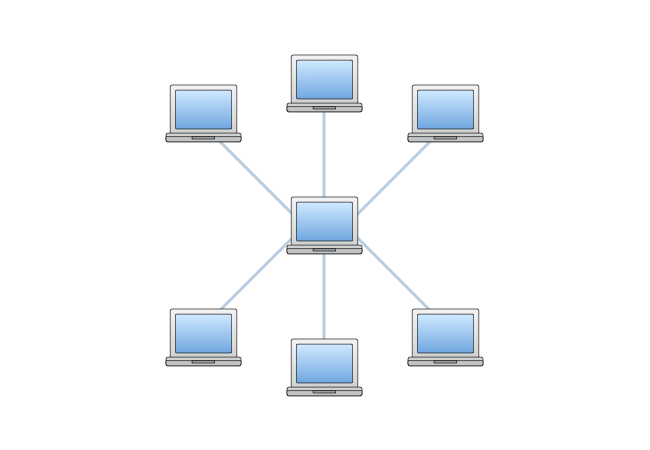
Star topology: All the devices are connected to a central switch or server.
| Advantages: | Disadvantages: |
| If a device fails or a cable is disconnected, the whole network is unaffected. | In a wired network, every device needs a cable to the central switch or server. This can be expensive. |
| It is simple to add more devices | If there is a problem with the switch or server then the whole server is affected. |
| Better performance than other set ups. Data goes straight to the central device so all devices can transmit data at once and there are few data collisions. |
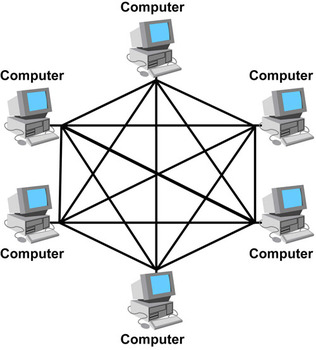
Mesh topology:
- Full Mesh: Every device is connected to every other device:
- Partial Mesh: Not all devices are fully-connected:
A Mesh topology is a decentralized networking devices that are either directly or indirectly connected without the need for a central or switch
A Mesh network works by sending data along the fastest route from one device or another.
The main advantage of a mesh is that there is no single point where the network can fail. If one cable fails, then data is sent along a different route.
However, it is very expensive as you need a lot of wires to connect so many together.
Wi-Fi:
Official name of Wi-Fi is IEEE 802.11X. This is a set of protocols that define how networks devices can communicate wirelessly over radio ways. For example:
What frequency should the radio waves be?
How powerful should the transmitter be?
How can data be secured?
What should happen if data is lost in transmission?
Frequency and channel bands?
Wi-Fi transmits data using radio waves in frequency bands:
- 2.4GHZ – There are 13 channels in this band. Only three of these channels do not interfere with each other. This means that the 2.4GHz range is not effective at supporting many networks
- 5GHZ – There are 24 non-overlapping channels in the GHz band. This makes the 5 GHz band much more effective for supporting a high number of networks.
Wi-Fi Encryption:
There are three common security measure to protect against this:
- Wired Equivalent Privacy (WEP) – Is the weakest protection of all. Needs a password to join the network. No data is encrypted, so it can be easily intercepted.
- Wi-Fi Protected Access (WPA) – Needs a password to join the network. Uses encryption to scramble the data being sent. Stronger than WEP.
- Wi-Fi Protected Access version 2 (WPA2) – Uses a stronger encryption algorithm then WPA to prevent unauthorized parties from accessing the encrypted data.
Ethernet: This is a protocol that defines how data should be physically transmitted between network hardware. This used in wired networks.
IP Address: This is a 32-bit number written as a 4 decimal number. The IP address can change meaning it is dynamic.
Exam Note: At GCSE, IP addresses are said to be dynamic. In reality, they can be static as well.
Mac Address: This is hard-coded into a network device. It is a 12-digit hexadecimal number. This is used to make sure the correct data is sent to the correct network device.
Network Protocols: (This is a set of rules that define how data is transmitted between connected devices)
- Transmission Control Protocol (TCP) – This is the protocol which dictates how data is sent between networks. It splits data from applications into small piece called packets and reassembling the packets back into the original data.
- Hyper Text Transfer Protocol (HTTP) – Used by web browsers to access websites and communicate with web servers.
- HTTP Secure (HTTPS) – A more secure version of HTTP. Encrypts all information send and received.
- File Transfer Protocol (FTP) – Used to access, edit and move files between devices on network.
- Post Office Protocol Version 3 (POP3) – Used to retrieve emails from server. The server holds the email until you download it, at which point it is deleted from the server.
- Internet Message Access Protocol (IMAP) – Used to retrieve emails from a server. The server holds the email until you delete it. You download a copy. This is used by most web-based clients.
- Simple Mail Transfer Protocol – Used to send emails. Also used to transfer emails between server.
Layers: A layer is group of protocols which have similar functions.
Layers are self-contained, protocols in each layer do their job without knowing what has is happening in the other layers.
Each layer provides a base for the layer above. It does hidden work needed for an action for the layer above it.
- Layer 4 – Application layer: Provides user access to applications, websites, files, emails. (HTPP, FTP, SMTP)
- Layer 3- Transport Layer– Controls data flow. Packet switching, for example, splitting data into packets and checking if they are correctly sent and delivered. (TCP)
- Layer 2 – Network Layer – Making connections between networks. It provides the routing of data across the network by making use of addressing. (IP)
- Layer 1 – Data Link Layer – Provides the physical transport and data through electrical signals. (Ethernet)
Advantages of using Layers:
- It breaks network communication into manageable pieces. This helps developers concentrate on only one area of the network without the other layers being affected.
- As Layers are self-contained, they can be changed without the other layers being affected.
- Having set rules for each layer forces companies to make compatible, universal hardware and software. This means that different brands will work with each other and always work in basically in the same way.
Packet Switching: This is used to direct data.
Packet switching is used by routers to direct data packets on the internet and other IP networks.
- Step 1) The data is split into packets ready to be sent across the network.
- Step 2) Each packet is given a sequence number (or packet number) to show the order of data.
- Step 3) Each router reads the packet header and decides which route to send the packet next, according to the IP rules.
- Step 4) The packets find their own way to their destination (mostly likely the fastest route) depending on network traffic.
- Step 5) As the packets take different routes, they can arrive in a completely different order. The receiving device uses the sequence number to resemble them in the correct order.
- Step 6) If the packets go missing in transit. The receiving device checks periodically that all packets have been received. If they have not been sent in a certain time, then it sends a timeout message back to the sending device.
- Step 7) If all the data matches the check sum, a receipt confirmation is sent to the sending device.
Packet switching: is and efficient use of the network because they are so many possible routes that data can take – packets can reach their receiving device even if there’s heavy traffic.
What’s inside a packet?
- Data – The data itself.
- Header – This is divided into three parts:
- Sequence number – as data is split into packets, the sequence number allows to file to be rebuilt in the correct order.
- Return address, when data arrives, the sender can be notified that the packet arrived safely. However, if a packet arrives corrupted, then the sender can be asked to send the data again.
- Destination Address – The data packets needs a destination address so it can be routed to the correct location.
- Error Check – This is always known as a checksum number. This is made up of a calculation and its correct answer. Once the packet has been received by the destination computer, if the calculation is run and produces the correct answer then we know that the packet has not been corrupted.
![]()